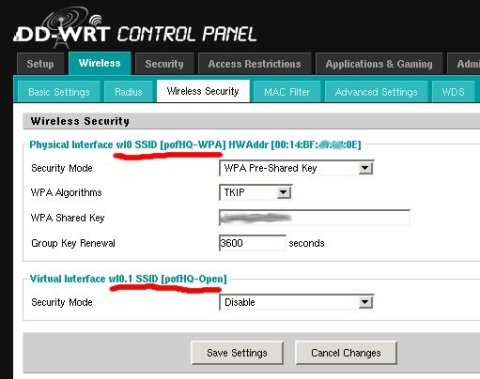
Ecco alcune specifiche tecniche della Fonera, prese dal blog di Martin Varsavky:
-
Chipset: Atheros 2315;
-
Sistema Operativo: OpenWRT
-
Kernel 2.4
-
Memoria Flash: 4 Mb.
-
Memoria SDRAM: 16 Mb.
-
Standard di emissione: 802.11b/g
La Fonera è prodotto dalla Accton.
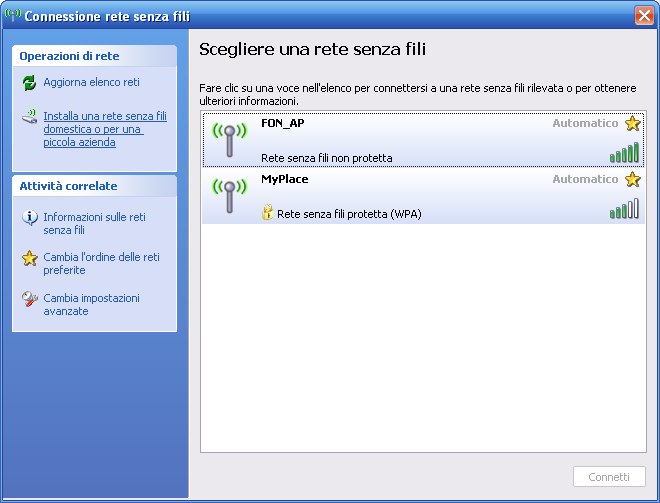
Iniziamo con uno scan sul vecchio Linksys, eseguito dal portatile collegato in Wireless, sempre al Linksys:
ipconfig
Configurazione IP di Windows
Scheda Ethernet Connessione rete senza fili:
Suffisso DNS specifico per connessione: key.chillispot.org
Indirizzo IP. . . . . . . . . . . . . : 192.168.182.2
Subnet mask . . . . . . . . . . . . . : 255.255.255.0
Gateway predefinito . . . . . . . . . : 192.168.182.1
nmap -P0 -O 192.168.182.1
Starting Nmap 4.11 ( http://www.insecure.org/nmap ) at 2006-10-01 19:19 ora sola
re Europa occidentale
Warning: OS detection will be MUCH less reliable because we did not find at lea
st 1 open and 1 closed TCP port
Interesting ports on 192.168.182.1:
Not shown: 1679 filtered ports
PORT STATE SERVICE
53/tcp open domain
MAC Address: xx:xx:xx:xx:xx:xx (Cisco-Linksys)
Device type: general purpose
Running: Linux 2.4.X|2.5.X
OS details: Linux 2.4.0 - 2.5.20 w/o tcp_timestamps, Linux 2.4.22 (x86) w/grsecu
rity patch and with timestamps disabled
Nmap finished: 1 IP address (1 host up) scanned in 37.122 seconds
E ora uno scan alla Fonera, sempre dal portatile connesso in wifi:
ipconfig
Configurazione IP di Windows
Scheda Ethernet Connessione rete senza fili:
Suffisso DNS specifico per connessione: lan
Indirizzo IP. . . . . . . . . . . . . : 192.168.20.177
Subnet mask . . . . . . . . . . . . . : 255.255.255.0
Gateway predefinito . . . . . . . . . : 192.168.20.200
nmap -P0 -O 192.168.20.200
Starting Nmap 4.11 ( http://www.insecure.org/nmap ) at 2006-10-01 19:33 ora sola
re Europa occidentale
Insufficient responses for TCP sequencing (2), OS detection may be less accurate
Insufficient responses for TCP sequencing (0), OS detection may be less accurate
Insufficient responses for TCP sequencing (1), OS detection may be less accurate
Interesting ports on 192.168.20.200:
Not shown: 1677 closed ports
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
8080/tcp open http-proxy
MAC Address: xx:xx:xx:xx:xx:xx (Unknown)
No exact OS matches for host (If you know what OS is running on it, see http://w
ww.insecure.org/cgi-bin/nmap-submit.cgi).
TCP/IP fingerprint:
SInfo(V=4.11%P=i686-pc-windows-windows%D=10/1%Tm=451FFC0D%O=53%C=1%M=001884)
T1(Resp=Y%DF=Y%W=1A5E%ACK=S++%Flags=AS%Ops=MNW)
T1(Resp=Y%DF=Y%W=1A5E%ACK=O%Flags=A%Ops=)
T2(Resp=N)
T3(Resp=Y%DF=Y%W=1A5E%ACK=S++%Flags=AS%Ops=MNW)
T3(Resp=Y%DF=Y%W=1A5E%ACK=O%Flags=A%Ops=)
T4(Resp=Y%DF=Y%W=0%ACK=O%Flags=R%Ops=)
T5(Resp=Y%DF=Y%W=0%ACK=S++%Flags=AR%Ops=)
T6(Resp=Y%DF=Y%W=0%ACK=O%Flags=R%Ops=)
T7(Resp=Y%DF=Y%W=0%ACK=S++%Flags=AR%Ops=)
PU(Resp=Y%DF=N%TOS=C0%IPLEN=164%RIPTL=148%RID=E%RIPCK=E%UCK=E%ULEN=134%DAT=E)
Nmap finished: 1 IP address (1 host up) scanned in 26.532 seconds
Per ora è tutto. Ho messo tcpdump ad analizzare il traffico passante per il router Linksys, cui è collegato in cascata la Fonera. L’ho lasciato per un’ora circa, fra poco controllerò se e come la Fonera telefona a casa…